Details
-
Bug
-
Resolution: Duplicate
-
Major
-
None
-
10.11.9, 11.10.3
-
None
-
Easy
-
Description
I'm not sure if the following vulnerability (from 2012) has been caught as I found and tested it on two recent versions of XWiki. Sorry if I create a duplicate.
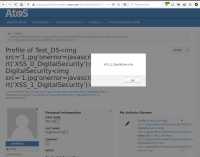
Several stored XSS vulnerabilities are present on XWiki. To create them, you just need to create a user account, without any particular rights, which is possible for an anonymous person on the Internet.Several stored XSS vulnerabilities are present on XWiki. To create them, you just need to create a user account, without any particular rights, which is possible for an anonymous person on the Internet.
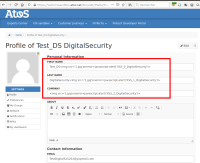
The vulnerable settings are located on the user's profile page. When editing the user's profile, the following parameters, sent in a POST request, are vulnerable. The tests were performed with the user *TestDigitalSecurity*.
- request : POST /bin/preview/XWiki/TestDigitalSecurity
- vulnerable parameters identifed (version 11.10.3):
- XWiki.XWikiUsers_0_first_name
- XWiki.XWikiUsers_0_last_name
- XWiki.XWikiUsers_0_company
- XWiki.XWikiUsers_0_phone
- XWiki.XWikiUsers_0_blog
- XWiki.XWikiUsers_0_blogfeed
Other parameters could de concerned on other version.
This vulnerability has been public since the year 2012 :
https://www.exploit-db.com/exploits/20856
During the tests, payloads allowing the opening of pop-up display were realized and are always visible at the following address:
https://xwiki.fsisandbox.atos.net/bin/view/XWiki/TestDigitalSecurity?category=profile
It is also possible to redirect to an external site using the following payload:
<img src='1.jpg'onerror=javascript:window.location='https://www.digital.security/fr/';>
Once created, the payload remains stored on the server. Any user, authenticated or not, who visits the victim user's profile page (where the payload is located) will trigger the JavaScript code.
With these stored XSS, a malicious user can craft a payload for various purposes, which include :
- have the victim's browser execute any JavaScript code
- redirecting a user to a website controlled by an attacker ;
- getting some information about the victim (like their operating system) ;
- creating forms to fool a user who will send its credentials ;
- making requests and actions on the user's behalf and without their intent and full knowledge;
- etc.
Attachments
Issue Links
- duplicates
-
XWIKI-17374 XSS Cross Site Scripting
-
- Closed
-