Details
-
Bug
-
Resolution: Duplicate
-
Critical
-
None
-
12.10.8
-
None
-
Created with latest Docker:MySQL combination as per Github steps
https://github.com/xwiki/xwiki-docker
-
Easy
-
N/A
-
N/A
-
Description
The application allows standard users to insert malicious Javascript into their profile via the 'My Dashboard' feature and the HTML macro.
User is freshly created and only a member of XWikiAllGroup and all changes are made in the context of this user.
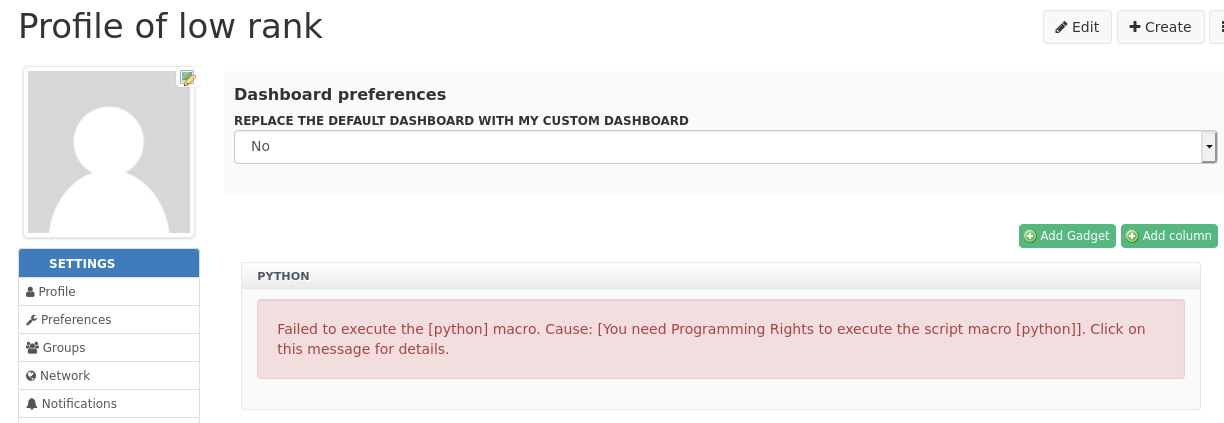
The HTML macro is not restricted by the 'ProgrammingRights' permission as is the Groovy or Python script macro. See below.
import os print(os.popen("id").read()) print(os.popen("hostname").read()) print(os.popen("ifconfig").read())
The above code inserted into a Python Macro produces the below exception and UI error message when saved/executed.
org.xwiki.rendering.macro.MacroExecutionException: You need Programming Rights to execute the script macro [python] at org.xwiki.rendering.macro.script.AbstractScriptMacro.execute(AbstractScriptMacro.java:178) ... ...
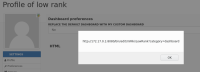
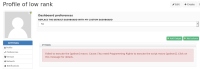
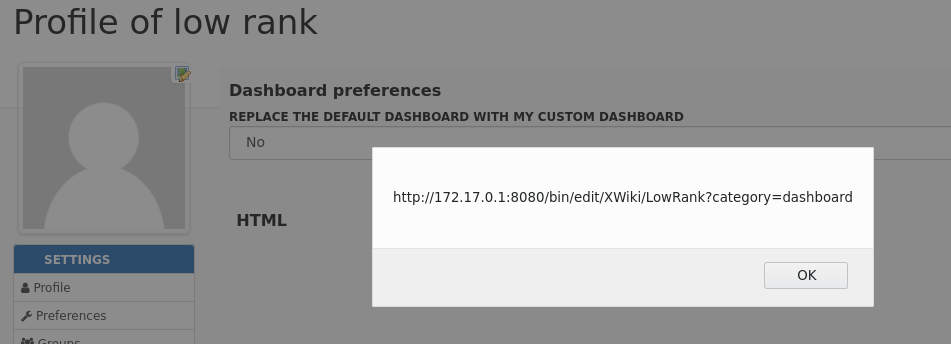
Creating an HTML macro with the below content results in code being executed as part of the HTML. This is executed by any user visiting the malicious users dashboard.
<script>alert(document.location)</script>
Recommendations
Limit access to HTML macro to authorised users via 'ProgrammingRights' or implement an allow-list of safe HTML. The former is likely the easier and safest option in light of the fact that the application allows code to be executed by administrative users anyway, this would appear to fit with the existing design pattern.
Attachments
Issue Links
- duplicates
-
XWIKI-18568 Multiple instances of stored cross-site scripting (XSS) via editor and HTML macro
-
- Closed
-