Details
-
Bug
-
Resolution: Duplicate
-
Major
-
None
-
None
-
Unknown
-
Description
An attacker can convince a victim to upload an attachment with a malicious filename in order to trigger an XSS vulnerability.
Below is a detailed replication guide.
1. Login in the XWiki instance and go to the following path `/bin/view/Main/#Attachments` and click on the Browse button. 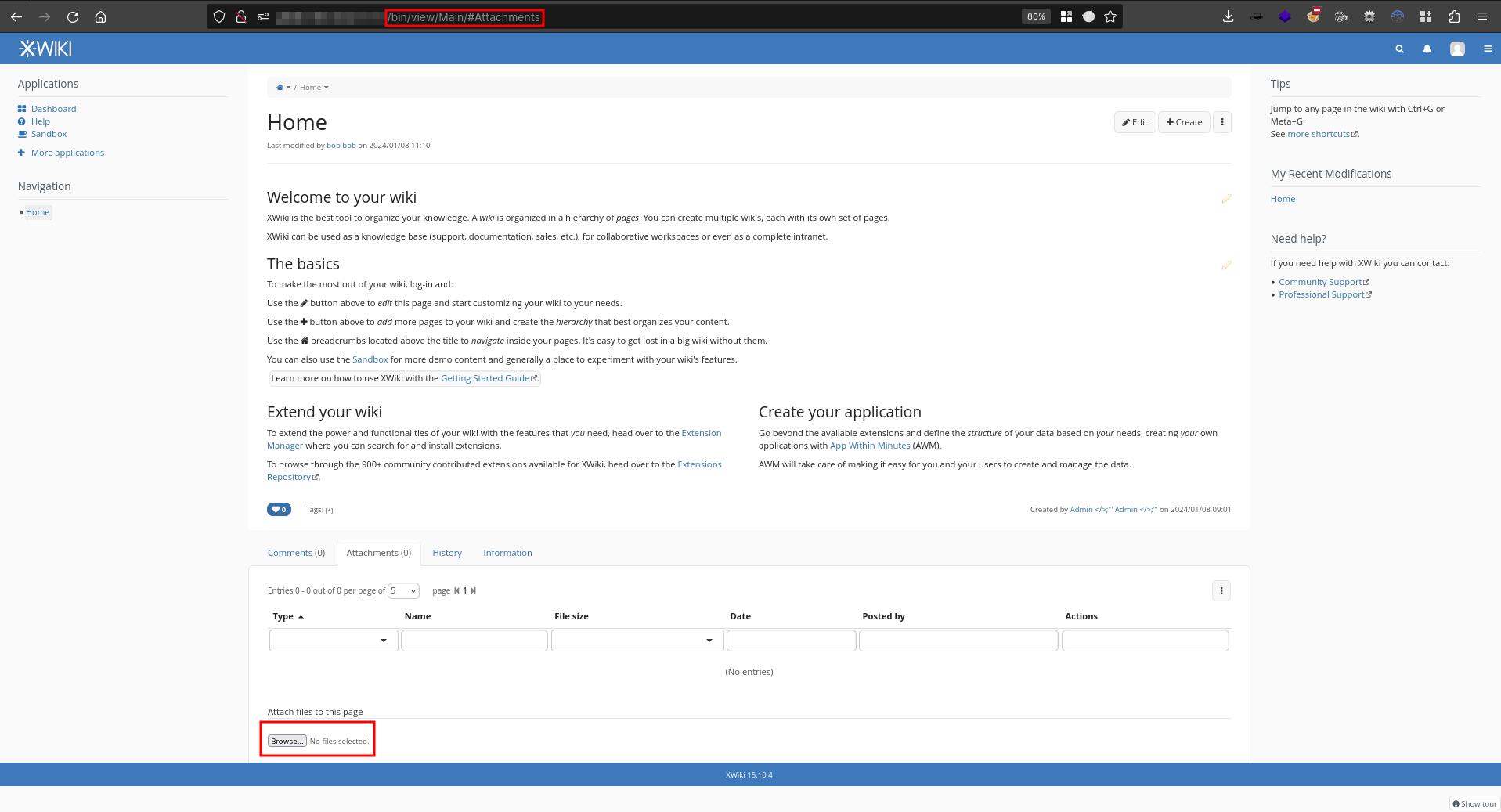
2. Upload a file with the following filename "><img src=x onerror='alert(1)'>.txt and it is going to trigger an XSS vulnerability
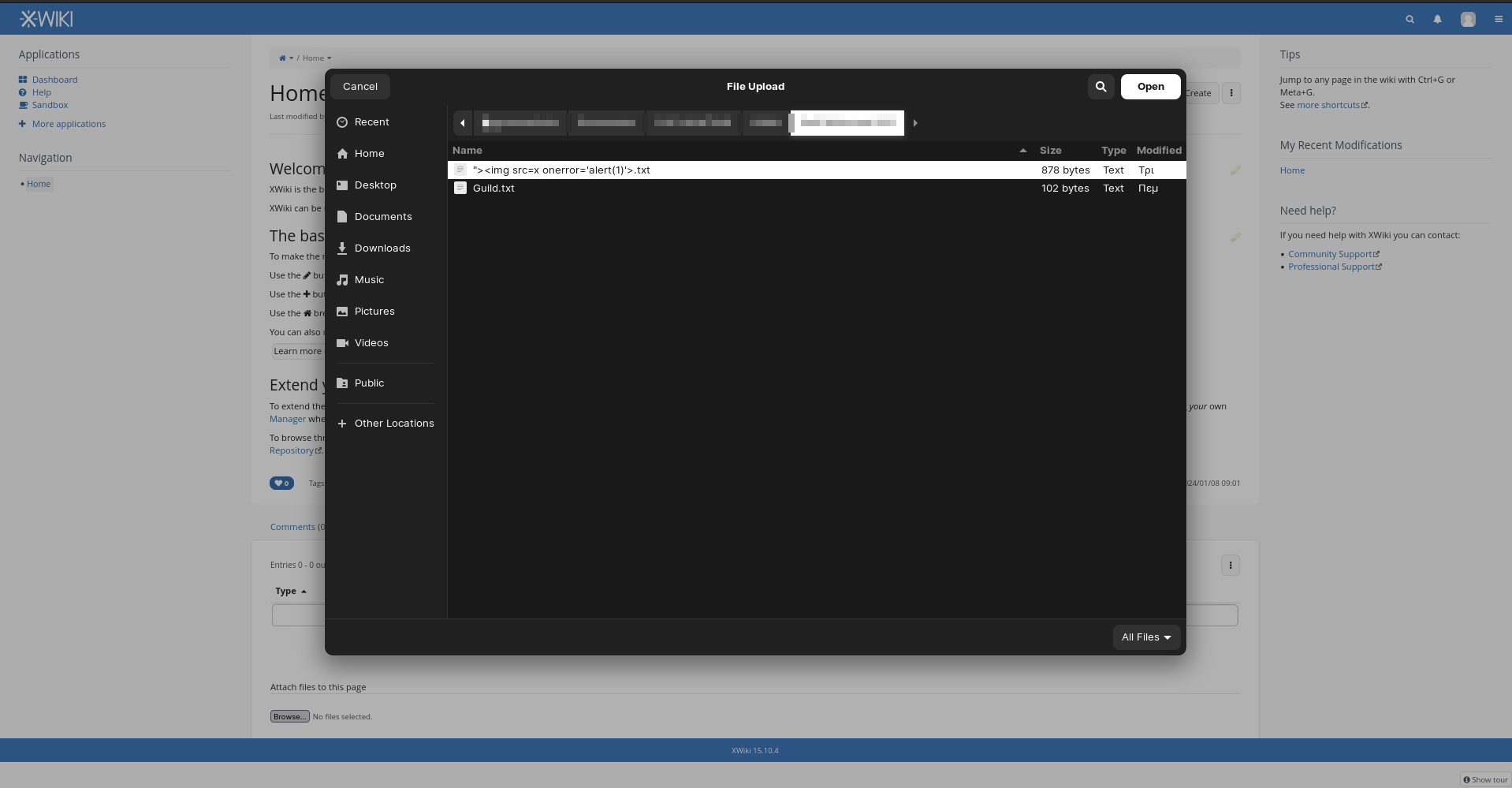
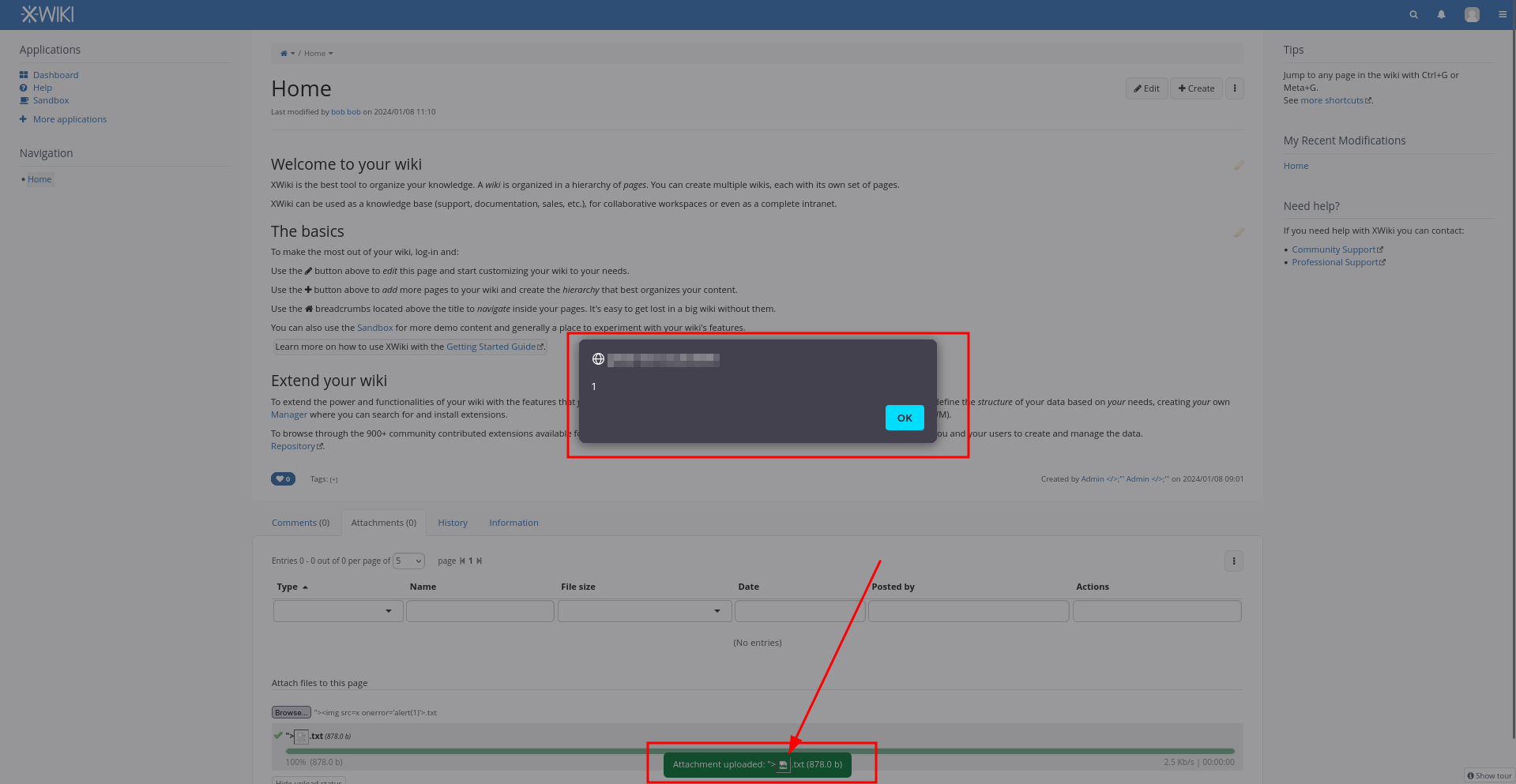
Attachments
Issue Links
- duplicates
-
XWIKI-19611 XSS through attachment filename in uploader
-
- Closed
-