Details
Description
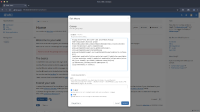
The {{groovy}} macro in XWiki allows execution of Groovy code on the server with the same privileges as the application process. In the tested configuration, no sandboxing or restrictions were applied, enabling remote code execution in multiple ways.
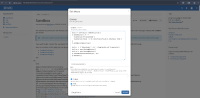
One approach was a pure Groovy reverse shell, created by using Groovy's direct access to Java networking and process APIs to open a socket back to an attacker-controlled host and bridge it to a command interpreter.
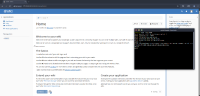
A second approach demonstrated that Groovy could also reach the underlying operating system: by writing a shell script containing a standard Bash reverse shell to the /tmp directory and then executing it, an outbound connection was established and relayed to the attacker.
In both cases, the outcome was a fully interactive reverse shell with the privileges of the XWiki process, allowing complete compromise of the underlying server.