Details
Description
SUBMISSION REFERENCES
- Submission code: XWIKI-E5JJ0KPS
- Submission URL: https://www.intigriti.com/auth/dashboard?redirect=/submissions/e95a7ad5-7029-4627-abf0-3e3e3ea0b4ce/XWIKI-E5JJ0KPS
RESEARCHER INFORMATION
- Submitter: floerer
SUBMISSION INFORMATION
- Created at: Fri, 04 Nov 2022 12:53:00 GMT
- Submission status: Archived
REPORT CONTENT
- Severity: Critical (9.0)
- Domain: https://intigriti.xwiki.com/ (Url)
- Proof of concept: XWiki allows users to use scripts like Python, Groovy and Velocity.
Normally only users with a lot of permissions are able to use these scripts since this is RCE by design.
However I think there is something really dangerous about this feature because any user is able to enter scripts into their own profile or in comments.
The user that places the payload will see an error like this: {883163}However when the admin want so edit the comment or the user profile the script is immediately executed when the inline editor is loaded.
So without knowing the admin can execute a very dangerous script.
*Steps to reproduce*
1. Login on your https://intigriti.xwiki.com account.
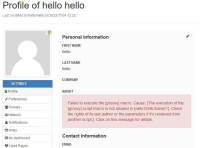
2. Go to your profile (by clicking in the top right corner on your profile picture) and then on this page click on the edit pencil of you `personal details`
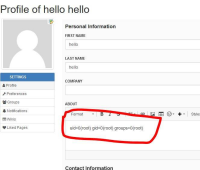
3. In the `about` section click on `Source` and then paste the following payload:
```
groovy
def cmd = "id".execute();
println("${cmd.text}");
/groovy
```
4. Click on `Save & View` at the bottom and you will see that you will get an error message since you are not allowed to execute this script.
5. You can also paste these scripts in comments, basically in al places where you have such an text editor. Once an admin tries to edit your page the script will execute automatically and the following will be shown:
This means that the CMD command succesfully executed.
PS. I tested this on my local instance but for the `intigriti.xwiki.com` instance you need to get admin permissions to test this or you need someone from the xWiki team to check this out.
- Impact: Store RCE payloads in comments and in your profile. Whenever an admin tries to edit your comments or profile the RCE will execute.
- Personal data involved: No
- Endpoint: https://intigriti.xwiki.com/bin/edit/XWiki/<user>?editor=inline&category=profile
- Type: Remote Code Execution
- Attachments: Knipsel.jpg, RCE.jpg
Attachments
Issue Links
- depends on
-
XWIKI-21311 Introduce a required rights analyzer
-
- Closed
-
-
XWIKI-21573 Enable the required rights analysis by default
-
- Closed
-
- relates to
-
XWIKI-20385 Privilege escalation/RCE via the edit action
-
- Closed
-
-
XWIKI-20386 CSRF privilege escalation/RCE via the edit action
-
- Closed
-
- links to