Details
-
Bug
-
Resolution: Fixed
-
Blocker
-
9.4-rc-1
Description
SUBMISSION REFERENCES
- Submission code: XWIKI-JYQ2GU1E
- Submission URL: https://www.intigriti.com/auth/dashboard?redirect=/submissions/e95a7ad5-7029-4627-abf0-3e3e3ea0b4ce/XWIKI-JYQ2GU1E
RESEARCHER INFORMATION
- Submitter: renniepak
SUBMISSION INFORMATION
- Created at: Wed, 09 Nov 2022 14:28:57 GMT
- Submission status: Archived
REPORT CONTENT
- Severity: Medium
- Domain: https://intigriti.xwiki.com/ (Url)
- Proof of concept: Hi XWiki team,
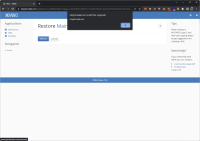
I found a Reflected Cross-Site Scripting vulnerability in the restore.vm template.
-
- Reproduction
1. Navigate to: https://intigriti.xwiki.com/xwiki/bin/view/XWiki/Main?xpage=restore&showBatch=true&xredirect=javascript:alert(document.domain)
2. Click the cancel button.
-
- Result
As soon as the cancel button is clicked our XSS payload triggers:
{709359}Vulnerable code snippet:
- Impact: If an attacker can control a script that is executed in the victim's browser, then they can typically fully compromise that user. Amongst other things, the attacker can:
- Perform any action within the application that the user can perform.
- View any information that the user is able to view.
- Modify any information that the user is able to modify.
- Personal data involved: No
- Recommended solution: In general, effectively preventing XSS vulnerabilities is likely to involve a combination of the following measures:
- *Filter input on arrival.* At the point where user input is received, filter as strictly as possible based on what is expected or valid input.
- *Encode data on output.* At the point where user-controllable data is output in HTTP responses, encode the output to prevent it from being interpreted as active content. Depending on the output context, this might require applying combinations of HTML, URL, JavaScript, and CSS encoding.
- *Use appropriate response headers.* To prevent XSS in HTTP responses that aren't intended to contain any HTML or JavaScript, you can use the Content-Type and X-Content-Type-Options headers to ensure that browsers interpret the responses in the way you intend.
- *Content Security Policy.* As a last line of defense, you can use Content Security Policy (CSP) to reduce the severity of any XSS vulnerabilities that still occur.
- Endpoint: https://intigriti.xwiki.com/xwiki/bin/view/XWiki/Main?xpage=restore&showBatch=true&xredirect=javascript:alert(document.domain)
- Type: Reflected Cross-Site Scripting
- Attachments: Screenshot 2022-11-09 152607.png
Attachments
Issue Links
- depends on
-
XWIKI-20583 Provide a macro for sanitizing URLs in templates
-
- Closed
-
- is caused by
-
XWIKI-13164 Be able to also restore deleted children pages when restoring a parent nested page
-
- Closed
-