Details
-
Bug
-
Resolution: Fixed
-
Blocker
-
11.8-rc-1
-
Unit
-
Unknown
-
N/A
-
N/A
-
Description
Steps to reproduce:
- As admin, edit a document. Perform some changes but do not save yet.
- As a user without script right in another browser context, edit the same document, dismissing the conflict warning. Add <script>alert('XSS')</script> in the content and cause a conflict, e.g., by deleting everything else. Save the document.
- As admin, save the document.
- In the conflict popup, select "Fix each conflict individually"
Expected result:
The conflict is displayed but no alert.
Actual result:
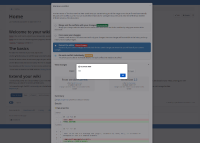
An alert with content "XSS" is displayed.
I suspect this is a result of missing escaping in https://github.com/xwiki/xwiki-platform/blob/b6080ac1552e6c1c19a709d07df1bf94414200d5/xwiki-platform-core/xwiki-platform-web/xwiki-platform-web-templates/src/main/resources/templates/diff_macros.vm#L85. This may also allow XWiki syntax injection if the conflict is displayed in a context with XWiki syntax support. This code has been introduced in XWIKI-16464, thus the affects version of 11.8.
The following screenshot shows the attack in action. Here, I added alerts in both versions but it is sufficient to have one of them, the example triggers two alerts, the shown alert is from the other save:
Attachments
Issue Links
- is caused by
-
XWIKI-16464 Merge conflict: allow choice by chunks and custom fixes
-
- Closed
-
- links to